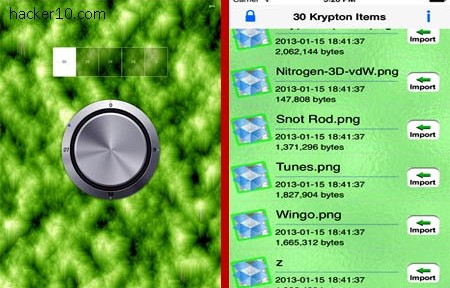
Krypton is a Mac OS and iOS (iPhone, iPad) tool to securely encrypt your files using AES256-bit in Cipher Block Chaining mode (CBC). This program is able to encrypt any kind of file, from documents, to images, videos or MP3s and full folders. If you are familiar with Truecrypt you will notice that Krypton works in the same fashion creating an encrypted storage space, called vault, that holds any file you place inside it and makes the whole vault unreadable without entering the correct password.
In a Mac computer you can use Truecrypt for free but iOS mobile devices do not work with it, Krypton will minimize work when transferring encrypted data in between secure vaults from your iPad or iPhone to your desktop Mac OS.

When you copy text to the clipboard this can be automatically sent to Krypton for encryption, and if you select a file for encryption it is possible to tick a checkbox to shred it after it has been secured and make recovery of the original data left behind impossible.
The software menu has a shortcut to send encrypted documents to Dropbox cloud space, encrypting files before uploading them is a good way to protect yourself from NSA spying as Dropbox can access or be compelled to access your data. Another two shortcuts in Krypton’s menu let you decrypt a file or folder, export it outside the vault and delete it from the vault.
The developers claim that if you lose your password the encrypted data is not recoverable so there is no backdoor, this looks like a good security tool due to the developers using a standard strong encryption algorithm like AES256-bit and the cross compatibility in between mobile and desktop devices.
You need to be aware that once the data has been exported outside the vault and accessed by another application it will no longer be encrypted and that other application could create a temporary copy that will be stored unencrypted outside the secured space, like for example, Time Machine Mac OS backup could contain a copy of decrypted confidential files.
Krypton will be best used in conjunction with a data shredder to securely delete any files leaking out of the encrypted storage space while you edited or viewed with them.