According to the RCMP newsletter, after two and half years of trying to get in, Canadian police in Saskatchewan has managed to crack a hardware encrypted device storing child porn inside, this is the first time the police has managed to crack this particular device.
An article in “The Star Phoenix” also mentions that two Datalocker external hard drives were cracked, the brand of the drive is further confirmed by “Gazzete“, the Royal Canadian Mounted Police magazine (link below), their article about this case does not name the company but the photo in the article clearly shows a Datalocker device.

According to the police magazine, Datalocker destroys the encryption key after 10 failed attempts but the forensic team overcame this challenge. Sgt. Joel Bautista figured out that given the maximum password length and variable characters that DataLocker allows for, the police computer cluster could brute force the password in around 10 years at most, so they kept trying.
Datalocker key entry does not support upper case letters, only small case and special characters are allowed, this limits passphrase strength.
Datalocker CEO, Jay W King, has contacted me acknowledging that Canadian police asked Datalocker for assistance in this case and he claims that the company only disclosed “publicly available information in regards to our password rules“. He also claims that the device had no brute force protection and asked me to remove what he says is wrong information and not to use the word “cracked”.
I agreed to change the picture of the post as it was featuring a model that did not exist at the time, the post now displays the correct model, but I will not change the text.
The police forensics team says that they had to overcome brute force protection, I have no reason to believe the police is lying or wrong. And to avoid misunderstandings, I am going to quote in bold what the Canadian police magazine says word by word:
“The forensic team had several challenges to overcome, including defeating the brute force counter, a feature on the device that would be initiated after exceeding a number of failed password attempts.”
Datalocker CEO also claims that the model pictured in the police magazine does not come with brute force protection, but another article in “The Star Phoenix“, says that there were two Datalocker drives involved in this case, it is possible that the police newsletter photo is not showing both of them.
The CEO has also sent me an old prospectus, and he is correct that the Datalocker Personal and Pro are advertised as not having self-destruct mode, but, a third column in the same prospectus, reproduced below, shows a model called Datalocker Enterprise, encrypted using AES256bit, listed as having self-destruct mode.
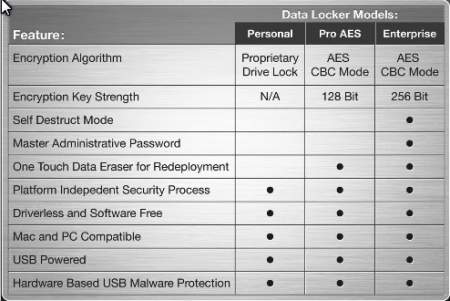
I am not going to argue about what device was involved in this case, because I honestly don’t know, but I can say for certain that the police claims that they had to “defeat the brute force counter“, textual words.
I am sorry man, but that is what the police says, I can’t change it. I invited Datalocker CEO to post whatever he likes in the comments section if so he wishes.
Sources:
RCMP police magazine: http://publications.gc.ca/collections/collection_2015/grc-rcmp/JS62-126-77-1-eng.pdf
Star Phoenix Story: http://www.thestarphoenix.com/technology/police+should+have+found+more+child+porn+evidence+gryba/11408124/story.html
