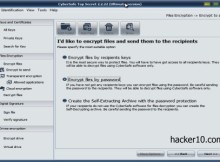
CyberSafe Top Secret is a commercial program made in Russia to encrypt files, folders and partitions, it can be used to create virtual encrypted drives or encrypt a full partition or removable media (USB thumbdrive) where everything stored is automatically ciphered. The program’s source code is available for download from the company website to reassure you that there is no backdoor.
The free edition of CyberSafe Top Secret should be considered trial software, the password length limit of 4 characters and DES algorithm make it very easy crack, it is only after buying the program that you get full protection with encryption algorithms that no law enforcement or sophisticated spies can penetrate.
I found the program very versatile, it has so many options that if you have not used encryption before learning how to use digital certificates for encryption and signing files could take a few days to learn for newbies but a PDF manual explains in detail how everything works, it is not difficult, it simply takes time.
I welcomed the addition of being able to encrypt files in your computer before uploading them to Dropbox, Google Drive and other cloud services. Google Drive, like Gmail, scans your data to find out if you have uploaded child pornography photos by matching the unique hashes of those files with the ones given to them by law enforcement. You have no guarantee that the NSA will not order Google to also scan your files to find X, once built-in scanning exists,nothing stops the NSA from abusing that capability for their own purposes. Anybody storing files in the cloud would be insane not to encrypt their files first and CyberSafe Top Secret allows you to do that easily dragging and dropping folders inside a window.
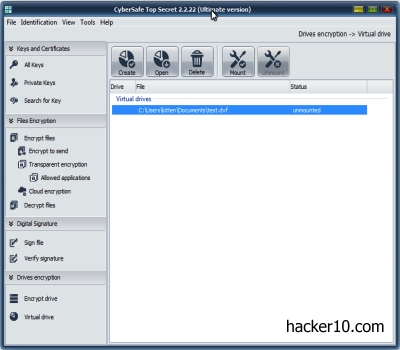
When creating a virtual encrypted drive (.dvf) you are given the choice of encrypting it with the USA Department of Defense approved AES algorithm or the Russian government standard GOST symmetric block cipher. Be careful when entering the password because you will not be asked for confirmation. This was bizarre, it is one of the few times that I come across an encryption program that does not ask you to confirm your password twice when creating an encrypted container that is meant to be uncrackable.
CyberSafe Top Secret Ultimate comes with a few business friendly features, like the optional Google Authenticator that can be activated in settings, a one time password mobile app that has to be used together with a user password before you can launch the program.
The heavy reliance on public key encryption to secure files suggests CyberSoft Top Secret has businesses in mind. It is easier to manage a central registry of digital certificates that can be revoked over the network than managing dozens of passwords, the program allows you to access a public key server and import or export a public encryption key without having to open your web browser.

My main criticism of this software is pricing, I obtained a license for the high end CyberSafe Top Secret Ultimate edition during a give away not connected to this review, otherwise, I would not have paid the €100 it costs. For slightly more money I can buy BestCrypt, WinMagic SecurDoc or SecurStar DriveCrypt Plus Pack full disk encryption.
There is a cheaper version of CyberSafe Top Secret but it comes with a maximum password length of 16 characters, I don’t think that is long enough to secure your data from an adversary with high resources and it seems unfair that security software you have paid for can come with a limit that weakens your security unless you buy their most expensive package.
CyberSafe Top Secret pricing can only be justified because it can manage and create encryption keys and it makes it easy to email to other people in a secure manner with a proven standard, but disk encryption wise, full disk encryption is much better.
CyberSafe Top Secret should be praised for making the source code available for download. This does not guarantee that the program is bullet proof but it guarantees that experts can look at how encryption works and detect changes if somebody forces the company to modify the code.
Perhaps if the price was cheaper for the Ultimate edition or if I needed support I would consider this program to encrypt my data. I see this software most suitable for a company with many employees after an easy solution to manage multiple encryption keys, home users in need of hard drive encryption might be better off looking at the other options mentioned above or with DiskCryptor (free), but if all you want is a solution to encrypt emails maybe it is worth to check out this software.
PS: After writing the review I noticed that the uninstaller is only in Russian, clicking on the default options erased everything properly. There is no malware, but it is not very professional not translating the uninstaller.