The following is a list of email services hosted in hidden services to send and receive anonymous email through Tor. A few of them can only be accessed using the Tor browser and have a Clearnet address only for information purposes.
If you are serious about security you must install the official Tor browser but if you are not paranoid about anonymity, you can download the Brave browser, this privacy browser is able to access .onion sites and Tor offering less security than the official browser, it has JavaScript enabled.
Cock.li (http://rurcblzhmdk22kttfkel2zduhyu3r6to7knyc7wiorzrx5gw4c3lftad.onion/): A free email and XMPP anonymous service funded with donations that allows registration with Tor , VPN and proxies. There are over a dozen domains to choose from when you sign up for a cock.li email address, other known domains used by this provider are Airmail.cc and firemail.cc
Morke (http://6n5nbusxgyw46juqo3nt5v4zuivdbc7mzm74wlhg7arggetaui4yp4id.onion/): Using the domain names Morke.ru and Morke.org with a SquirrelMail interface, registration is free but it can only be done using the Tor browser.
ProtonMail (https://protonmailrmez3lotccipshtkleegetolb73fuirgj7r4o4vfu7ozyd.onion): Fully encrypted Switzerland based privacy email provider that allows registration using Tor, the free version of ProtonMail provides for a decent service and includes extra features like an encrypted calendar, and cloud storage.
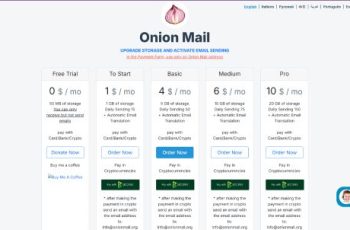
OnionMail.org (http://pflujznptk5lmuf6xwadfqy6nffykdvahfbljh7liljailjbxrgvhfid.onion/): Anonymous email provider that encrypts email with your own key, they have a multi language free service where you can test it and upgrade to a paid plan with more storage space, cryptocurrency is accepted and there is support live chat in their website.

OnionMail.info: Clearner directory listing OnionMail email providers, you have to be careful who you pick, nobody knows who is running the service and a few of them that I checked had the mail server misconfigured.
DanWin1210 (http://danielas3rtn54uwmofdo3x2bsdifr47huasnmbgqzfrec5ubupvtpid.onion/): Personal website providing free anonymous Jabber and email account that can be accessed in the clearnet or Tor.
CS email (http://csmail3thcskmzvjicww3qdkvrhb6pb5s7zjqtb3gdst6guby2stsiqd.onion/): Disposable email address with v3 Tor hidden access, ideal to receive registration email details or brief communications, you can reply using the interface but emails are only kept for one hour. Sponsored by VPN provider CryptoStorm.
Email providers that can be accessed with Tor
The following email providers do not have a .onion email address but are privacy and Tor friendly, you should be able to sign up for their webmail service using the Tor browser which will provide with nearly as much a privacy as accessing them using a hidden service.
MailFence: Based in Belgium, with support for PGP encryption and free plan. It is impossible for the email provider to read your emails if you use your own PGP encryption key.
Tuta: German email provider specialised in privacy, it has implemented quantum resistant encryption to future proof your privacy and metadata scrubbing.