Bitmessage is an open source P2P program utilizing a Bitcoin like protocol that instead of sending money sends anonymous encrypted messages to one or multiple people at once, the application has a portable mode that does not need installation, it uses 2048-bit RSA encryption keys stored inside a keys.dat file which can be opened with any text editor and OpenSSL for cryptographic functions. Bitmessage cryptic addresses closely resemble a Bitcoin address, the best part is that both keys are compatible, Bitmessage uses the other part public key to print their Bitcoin address in the console which can be used to send them money.
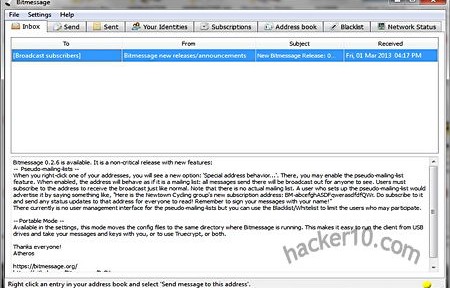
Bitmessage sends data over its own P2P network, the nodes store messages for two days before erasing them, new nodes joining the network will download and broadcast the pool messages from the last two days. To stop spam the sender is required to spend computational processing power for each message he sends, modelled like the Hashash antispam scheme and the Bitcoin mining system, the protocol has been designed to be scalable as needed. I sent a small text message to a friend and it only took a few seconds of wait for it to be processed, a “Doing work necessary to send message” warning will be displayed while you wait and your computer CPU works, I also subscribed to an open Bitmessage mailing list using the subscription tab by simply adding the address “BM-BbkPSZbzPwpVcYZpU4yHwf9ZPEapN5Zx”

Other tabs in the program allow you to blacklist and whitelist addresses, add contacts to your address book broadcasting to everyone listed there or selecting just one contact, the tabbed system makes Bitmessage usage spontaneously easy, you can also change the default listening port “8444” and network settings entering a Socks proxy, only the key management was very primitive, it opened up Bitmessage keys using Notepad.
You can create as many Bitmessage addresses as you like, creating and abandoning them is encouraged, there is an “Identity” tab from where to manage your addresses, they can be labelled. Addresses can be generated using random numbers or a passphrase, called “deterministic address“, you can recreate this address on any computer from memory without having to back up your keys.dat file as long as you remember your passphrase but you will need to know the passphrase to recreate the keys if you lose them, you will also need to remember the address version and stream number, choosing a weak passphrase could result in a brute force attack and your identity stolen, deterministic addresses can be made one or two characters shorter spending a few extra minutes of computational processing power, these addresses are optional, I believe the random cryptic addresses to be more secure for those paranoid.
Bitmesssages are first encrypted and then sent to a common message pool shared by all users to hide sender and receiver, only those listed in the receiving address will be able to decrypt and read them, the program has been designed to only send text without any attachments, I did not test it but theoretically it should be possible to send a jpeg photograph. After erasing a message there is no trash can to retrieve it but it will still be present in your hard drive to manually view it with a bit of work.
I used Bitmessage with a VPN and I did not experience any problem besides a coloured network status code that turned yellow indicating that my firewall or router couldn’t forward TCP connections, this is not a big problem, it only meant that my node was not relying messages to other nodes for other people but I could still receive and send them, as long as someone in the network has the green network status messages can be passed on in between peers.
Note: The sofware is currently a beta release in testing.