Mozilla Labs, the makers of Firefox browser and Thunderbird, have come up with an experimental browser based single login system called Mozilla Persona. After a user has verified his email address by visiting a link sent to his inbox he can claim ownership and use that email address and a chosen password to login at any site supporting Mozilla Persona, very few at the moment, you will know if a site supports Mozilla Persona when they show the logo.
The main advantages of Mozilla Persona are that it saves surfers from having to remember dozens of different usernames and passwords across sites, it does not leak information to the website you log in and it works across browsers, site authentication only needs Javascript enabled to work .
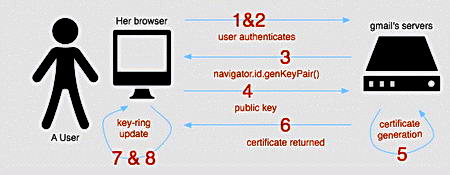
The Mozilla Persona website is used as authentication backend server holding user’s email details, but anyone can run their own verification server, Mozilla Persona is a decentralized login system. When a user logs into a Mozilla Persona identity provider a set of public/private encryption keys will be created inside the browser using javascript, the public encryption key is then sent to the Mozilla Persona identity provider where it will be used to sign an identity certificate before sending it to the user’s browser for storage.
Any website requiring a user to login using Mozilla Persona will use javascript to prompt the user if wishes to login, if he agrees the browser will send the previously stored browser identity certificate, digitally signed with that user’s private encryption key, the login server will verify the signature asking the Mozilla Persona identity provider for the user’s public encryption key, making sure the digital signature is valid.
The disadvantages of Mozilla Persona are that websites need to support it and since many already support OpenID, Google Account login, Twitter and Facebook connect, they will be wondering if they really need to add even more login plug-ins, another downside is that if your Mozilla Persona provider goes down you will be unable to login to dozens of sites. This is what happened to my OpenID provider some time ago and it was then that I made the decision not to use OpenID anymore, failure of the authentication server or a denial of service attack against the server constitutes a huge risk.
Mozilla Persona vs OpenID
OpenID is a more seasoned one click authentication system that shares some common ground with Mozilla Persona, both systems need a single username and password to login across multiple sites and act like a third party authentication server working across browsers, the main differences are:
- Mozilla Persona does not involve the identity provider in the login process whereas OpenID identity providers are part of the authentication process, this means that OpenID identity providers are aware of the sites you are a member of, Mozilla Persona protects your login activities from identity providers, OpenID does not.
- Mozilla Persona has been designed to tightly integrate with the browser with the login process taking part within it, a Firefox add-on is in the making, OpenID redirects you to a website for the login process to take place.
- Mozilla Persona always identifies users with their email address, OpenID authentication process does not always implicate a user email address.
Conclusion Mozilla Persona
I fail to see how Mozilla Persona is any better than a password manager, Mozilla Persona simplifies login across multiple sites by only needing a single password and a password managers will automatically fill in your username/password, not having to type it in, all you need to know is the masterpass, just like with Mozilla Persona ID.
Mozilla Persona can be a good replacement for those endangering their privacy using Facebook connect and Twitter accounts to login at other sites, by using Facebook connect you are giving third party companies access to private data, Mozilla Persona, like OpenID, will stop that, but I am not seeing myself using Mozilla Persona any time soon.
I am very happy with my offline password manager and I believe it is a much more secure login system than using a server that I have never seen or audited to manage my login credentials for dozens of sites.
Note: Mozilla Persona used to be called BrowserID, this post has been updated accordingly.

Leave a Reply