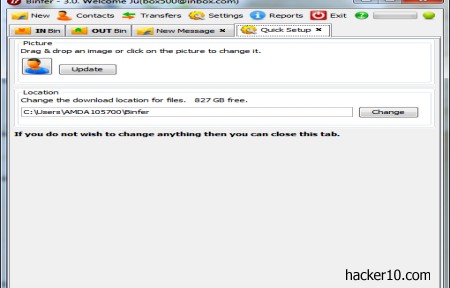
Binfer is a program to share large files without having to upload and download them like in FTP or a cloud online storage space. Binfer uses P2P technology, it only requires you to drag and drop the desired file on Binfer’s window and you will not have to encrypt or password protect the data, everything is automatically encrypted with AES128-bit, encryption keys are changed for each file transfer and there is no central server that could be compromised.
The software is written in Java, it works in any operating system, Windows, Mac or Linux, with an Android and Internet browser app to share files with others on your mobile device without having to install anything. But you will speed up the process if you have Binfer in your computer.
When you first install Binfer you will be prompted to create an account using a valid email address, if the welcome email they send you bounces, your account will be automatically deleted.
The interface various tabs look like the P2P program utorrent. In them you can monitor in and out file transfers, reports, see contacts and access a built in email client attaching files of any size to send to your friends for them to download clicking on the received link, but they will need to be using the same program to download it.
Binfer is a good solution for those who often share big files, similar Peerio to but with more functions.The only thing is that the free mode has a file size limit, you should look into Bittorrent Sync before parting with your money for Binfer.
Update: I have had a spammer in this blog linking to Binfer. I can’t prove who is behind this, other than to say all fake comments (now deleted) were made by IP 71.194.2.92 using different nicks.