Mumble is an open source VoIP program for group or P2P chat that runs in Windows, Mac and Linux, with iPhone and Android versions in beta. Mumble encryption is implemented with public/private key authentication and unlike Microsoft owned Skype, which supposedly also encrypts calls, in Mumble cryptography experts can scrutinise the code to make sure that the NSA has not inserted a backdoor or weakened the algorithm.
Mumble is widely used by gamers due to its low latency and background noise reduction resulting in superb audio quality, but you can use it for any kind of communication. Ninety per cent of the public chatrooms I visited where gaming clans and I had to manually add activist related Mumble servers like occupytalk. For high privacy group calls you have got to manage everything yourself, including the server, otherwise a rogue operator could carry out a man-in-the-middle attack to eavesdrop on you.

When you first install Mumble you will be prompted if you would like to run your own server (called Murmur) this will give you total control over who can access the chatroom but it requires staff and time. The other option is to join one of the dozens of public Mumble servers classified by countries and create there your own chatroom or rent a Mumble server from a specialist provider, they can be easily found with an Internet search for Mumble server hosting.
The Mumble client Audio Tuning Wizard helps you correctly set input levels for your sound card with voice activity detection and sound quality as well as optional text to speech to read typed in messages. Messages are read with a metallic voice but you have the option of buying a professional text to speech package from a third party and add it if you are going to use the feature a lot. The second Mumble client step creates a digital certificate to authenticate with servers. The most likely is that the servers you visit will have a free self-signed digital certificate poping up a warning window that you will have to accept before joining, this is not a huge security risk if you examine the certificate before accepting it and it only has to be done once.
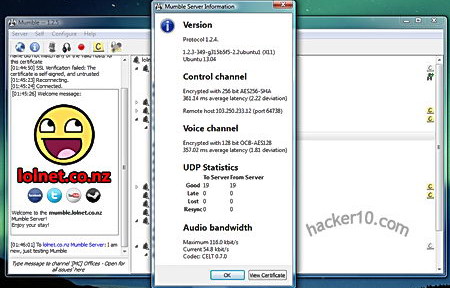
Besides AES256-bit encryption Mumble has the edge over other VoIP tools because it can communicate with the TCP protocol, this is absolutely necessary for any program to be tunnelled in Tor and most VoIP programs only work with UDP, Mumble also has very low bandwidth needs, it will not clog Tor nodes and it works as Push to talk (PTT), you need to push a button to transmit voice, instead of an always on call connection.
You can either connect directly to Tor running it in your computer and configure Mumble by going to Configuration>Network tick the checkbox that says “Force TCP Mode” and fill in the SOCKS5 proxy settings with localhost and 9050 for the port, or roll your own anonymous Mumble server for your friends renting a VPS, installing the Mumble server software in the VPS, configuring the server firewall to accept incoming connections in Mumble’s default port 64738, installing Tor in the VPS and from then on all voice calls made using that server will be encrypted and anonymous.