DropKey is a MAC OS X tool (Lion and above) to easily encrypt and share documents using public/private key encryption, you only have to drag and drop any file you want to encrypt on top of the DropKey icon that appears in the menu bar and it will automatically encrypted, specifying who to send the file to will create a new email message with the encrypted attachment, only the person whose public encryption key has been used will be able to view it.
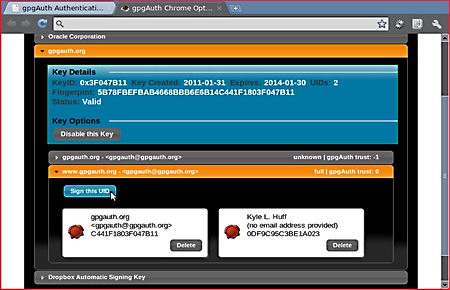
Your public encryption key is stored in your personal contact record in the Address Book and it can be safely attached to a vcard file (.vcard) to send to your contacts, any file encrypted by a sender using your public key can be opened by you without entering a password. The secret private key in your power decrypts it and makes sure that nobody else can access the file.
It is possible to guard against man-in-the-middle attacks, where an adversary sends the wrong public encryption key making you believe that it is that of your friend so that you encrypt your personal files using it. DropKey can generate 4 random dictionary words with each encryption key, asking the person you are communicating with to verify those words, over the phone or Instant Messenger, will guarantee that it is his key. This is akin to a digital fingerprint, formed of random letters and numbers, DropKey has pursued to make the system easier for the average user by using pronounceable words instead of random characters.
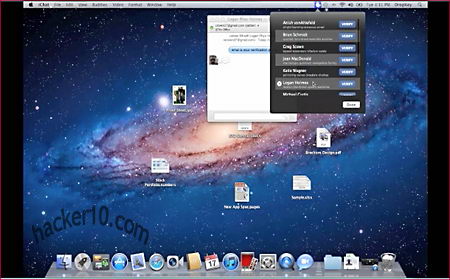
This program is very easy to use and it integrates with your address book, the private encryption key is kept in OS X’s built-in Keychain Access app, to see it you will be asked for the administrator password. DropKey can be used to keep personal files encrypted, they don’t have to be necessarily emailed, simply choose a place where to save the file after encryption, multiple files can be encrypted at once, the developer created this app with people wanting to email documents securely and not for those who need secure data archiving, functionality comes accordingly.
No data ever leaves your computer unencrypted, the encryption and decryption process takes places locally, the recipient will need to have DropKey installed but doesn’t have to buy the software just to decrypt data, trial mode decryption never expires. I can foresee a big problem with this app, you won’t be able to communicate with friends using Windows or Linux computers, and for that reason I would advise you against it and go for GPGTools instead, which is compatible with any other OpenPGP software.
Notice: Link updated to iTunes, original site is down, app is not free.