It is very hard to predict when a hard disk will fail, Acronis Drive Monitor is a free hard disk monitoring tool that will alert you before a hard disk crash. Acronis Drive Monitor will avoid data loss by monitoring the physical hard disk health using S.M.A.R.T. (Self-Monitoring, Analysis and Reporting Technology) readings and warning you before the drive fails.
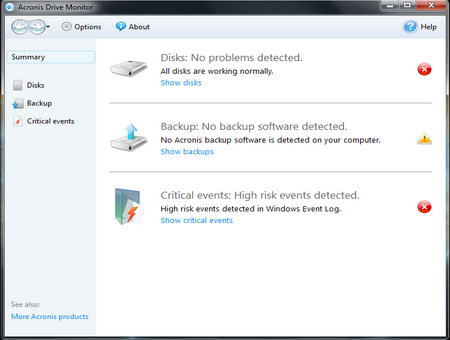
A colour coded summary provides an overview of the disk’s health at a glance, in addition, when it detects a problem it will generate an onscreen alert or send and email depending on configuration.
This free hard disk monitoring tool will warn you if no back up software has been found in the computer, it is inevitable that all hard disks will fail one day, nothing lasts forever, everyone should have a back up solution put into place it is highly responsible to warn users about this, even if Acronis is trying to push its paid for back up software in the process.
Acronis Drive Monitor main features
- Hard disk health monitoring in the background
- Monitoring of event logs for possible problems
- Email alerts in case of hard disk complications
- Weekly hard disk electromechanical status report
- Support for RAID hard drive configuration
This Acronis product integrates very well with the rest of the premium Acronis home and business software but you do not need to have any of those installed in order to use it, Acronis Drive Monitoring seems to have been released with the freemium market in mind, where people are given something for free with the hope that they will upgrade to a paid for product with more features.
This hard disk monitoring tool does an excellent job, is easy to use and it is on a par with paid for hard disk diagnostics software.