If are conscious about computer security or are using a public computer in an internet cafe or library, using some kind of protection against keyloggers is a must have.
A keylogger can easily capture your Yahoo mail and Gmail passwords as well as banking passwords, anything you type in your keyboard could be logged and stored by someone you don’t know.
Neo’s Safekeys keylogger protection is a virtual keyboard that works with the mouse and will protect you against malicious hardware and software keyloggers.
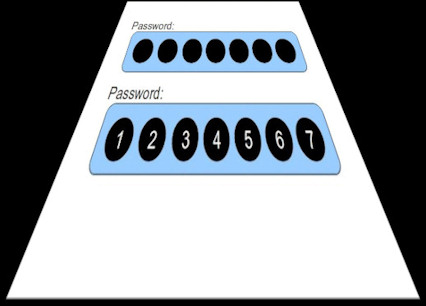
Do not be fooled by the Windows on-screen keyboard as it performs software key presses each time you click an on-screen key and even the most basic keylogger will capture everything you type using it.
Neo’s SafeKeys keylogger protection main features
Password drag and drop keylogger protection: This feature allows you to tansfer your password dragging and dropping the password from Neo’s SafeKeys to the destination program, there are no keyloggers at present that can capture a password while dragging and dropping it.
Keylogger screenshot protection: Neo’s SafeKeys keylogger protection protects you against screenshots being taken ofyour mouse movements, Neo’s SafeKeys introduces a protective transparent layer on the virtual keyboard, if any malware is taking screenshots they will only see the protective layer and not the virtual keyboard buttons, screenshots taken using Windows commands do not see the transparent Windows, Neo’s SafeKeys will always remain at least 1% transparent.
Field scrapping keylogger protection: Some commercial keyloggers can grab passwords from password fields using Windows API commands, Neo’s SafeKeys keylogger protection will keep your password away and it will never store it behind the asterisk mask in Windows fields.

Mouse positioning keylogger protection: Mouse position logging is often used to defeat people using the banking websites on-screen keyboards, each time you click the coordinates of your mouse are captured, since the virtual on-screen keyboard always has the same dimensions the malware can then learn what on-screen keys you clicked on.
Neo’s SafeKeys will always start in a different position on the screen and its height and width will also change. You can also use a button named Resize SafeKeys to reset your virtual keyboard dimensions.
Clipboard keylogger protection: Most malware is able to capture data copied to Widnows clipboard, that includes even passwords. Neo’s SafeKeys never uses the clipboard for anything, ever.
Neo’s SafeKeys keylogger protection extrea features
Neo’s SafeKeys allows for the creation of customized keyboard layouts, your settings (not the passwords) will be stored in a NSKconfig .ini file, you can copy it and edit to your own taste until you get the keyboard layout you want.
You can use Neo’s SafeKeys as a portable notepad, disabling the password mark you will be able to see anything you enter.

Hardware keyloggers like the one pictured above are notoriously hard to detect, antivirus will not find them and they work in all operating systems.