OnionMail is an open source mail server developed by hacktivists fighting mass surveillance, it runs on the Tor network and is able to communicate with the Internet as well as Tor hidden nodes.
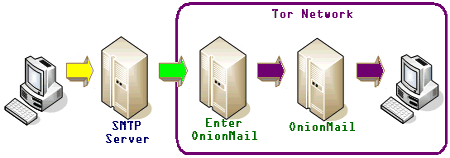
Running an OnionMail server and joining the federated network is open to everybody, connections in between servers are always encrypted with SSL, transition servers do not store any data, only in the final destination OnionMail server saves messages and it automatically erases them after reading or if they have not been picked up by the user in a period of days, using the wipe command (Linux) to make forensic recovery impossible.
An OnionMail email inbox is encrypted with RSA/AES asymmetric encryption keys and user passwords, data is then hashed and scattered around multiple OnionMail servers in the network, if a server is seized no meaningful information or metadata can be obtained. Another security feature is the ability to remotely nuke a server’s digital certificate, this is useful if an administrator loses physical access to the server, OnionMail checks the legitimacy of digital certificates in the network and servers not using a valid one will be disconnected.

OnionMail anonymous Tor email
In Tor you don’t have to worry about revealing your computer IP but a local email system clock can give away your approximate geographical location, to stop this, OnionMail spoofs your time zone, it will also spoof the PGP version you are using, helpful in case a vulnerability is discovered in a specific PGP release, an attacker would be unable to find out who is using it without testing everybody.
For internal email communications inside the Tor network you are assigned a cryptic .onion address, this is automatically transformed into a a clearnet comprehensible address using the Virtual Mail Address Translation protocol to append the .com/.net/.info of your Tor exit node so that people on Yahoo or Gmail can reach you.
For example, if you are using the onionmail.info exit node, your .onion email address will be transformed into test.serveraddress.onion@onionmail.info when you send an email message to the Internet. Spam is eliminated using custom blacklists that mail server operators can tweak.
You can find a few Tor email providers but they are not chained and their addresses can’t be used to contact people outside Tor. OnionMail stands out from the crowd uniting all email servers in a single network and allowing users to send and receive email to the Internet from within Tor.
More than a dozen OnionMail servers are listed in the homepage, to open an account you only need to select one of them with Tor installed in your computer, or download a python script that can be used in Tails to configure your email client. Windows users can download a beta version of OnionMail and the more technical advanced people can install OnionMail in a rooted Android device with Orbot, a free proxy app that runs Tor, the K9 Mail client, and APG, a PGP key manager.
OnionMail anonymous email
OnionMail does not hide that it has been specifically developed to stop the NSA and similar espionage agencies from following you. The developers know what they are up against and they make sure that their zero knowledge design will withstand rogue operators and mail server seizure, which leaves only a trojan horse or spearphising attack as the only way to get into your email account.
A very well designed, thought out email system with good documentation and help screenshots that has all a security paranoid person can wish for, anonymity, encryption, free and running on Tor.


Ninho
Thank you for this very readable account ! If it’s not to late for comments, I would ask a question : assuming onionmail operating as designed and advertised (no compromised or hacked server), and assuming mail exchanged from an onionmail account to another (no exit ti/entry from clearnet), and assuming for the moment that the sender does not add own encryption (GPG or similar) to their messages, will the original unencrypted message body be retrieved anywhere along the chain of onion routers involved in onionmail transmission and storage ? ICBW, but as I understand it under the above hypotheses, cleartext would be unencrypted – albeit transiently – at the site of sender’s onionmail server (SMTP). Right ? Can someone analyse deeper ?