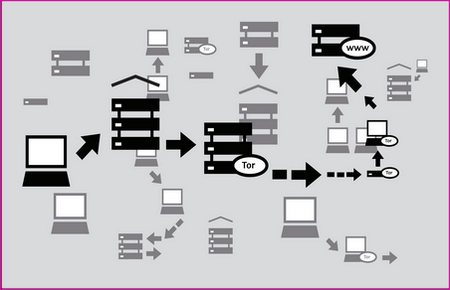
Tor-ramdisk is a tiny Linux distribution (5MB) developed by the IT department at D’Youville College (USA) to securely host a tor proxy server in RAM memory, it can run in old diskless hardware and it will stop a forensic analysis from people stealing or seizing a tor server. In the event that a tor server is seized due to ignorance or calculated harassment, and it would not be the first time, the end user would still safe because the chained nature of the tor proxy network makes it impossible to find out someone’s computer IP by seizing a single server but other data, even if meaningless, can still be recovered, running tor in RAM is an extra security step that can help convince people that the machine is merely acting as a relay as it contains no hard drive.
When a Tor-ramdisk server is powered down all the information is erased with no possibility of recovery, the tor configuration file and private encryption (torrc& secret_id_key) in between reboots can be preserved exporting and importing them using FTP or SSH making the life of a tor node operator easy.

One disadvantage of running a tor node entirely in RAM memory is that it can not host hidden services as that requires hard drive space, other than it is a fully functional entry,middle or exit tor node. I would advise you to block all ports (USB,Firewire) in the server with epoxy, there are computer forensic tools that can be plugged into the USB port and make a copy of the RAM memory on the fly. You might have heard about the cold boot attack where someone with physical access to a recently switched off server or computer can still retrieve data remanence from RAM memory, this is not easy to achieve and the recovery timespan is comprised of a few seconds.
Leave a Reply