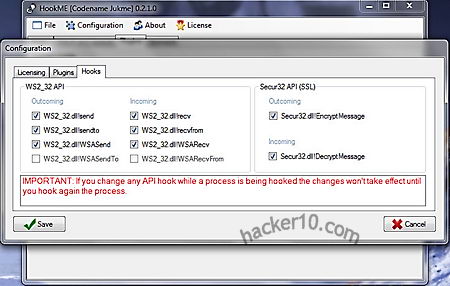
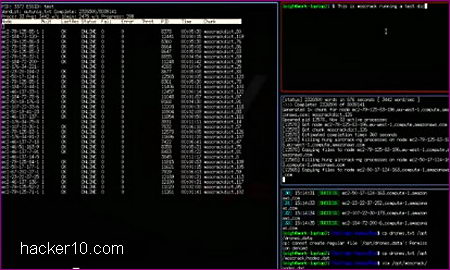
HookME is a free open source Windows tool to intercept network communications hooking up desired processes and API calls, including SSL clear data, the unencrypted SSL headers.
The software download is initially tiny (125Kb), when you try to install it you will get a message saying it requires supplemental .dll and .db files to work, over 30MB of files will be automatically downloaded by HookME from a third party site, you will also be asked to register the new .dll dependencies giving administrative rights to Windows Command Processor, the installation process could make some people feel uneasy about this tool containing malware, the only guarantee you have is that HookME is developed by well known OSINT FOCA creators.
Every time you start the software you will be shown a small Netkra Deviare unregistered license splash screen, you don’t have to buy a license but it will get rid of the initial screen if you do.

The software has a tabbed user interface that can be used to intercept any hooked API call and read the data that is being sent and received, you can change intercepted packets in real time, dropping or forwarding them, a Python plugin system allows for anyone to create their own custom addon, there are some templates for that. HookME developer showed in BlackHat Europe 2013 conference how to easily intercept MySQL data and inject a backdoor on the fly with a few clicks executing remote commands.
Real time intercepted data can be seen in the user interface Hex editor showing you hexadecimal numbers and their corresponding text meaning, you can highlight data packets and click on the “Drop” or “Forward” buttons, a small window below the program lets you know what process is hooked, for example it will show firefox.exe if you are eavesdropping on a Firefox browser session.
This tool can be used for penetration testing creating malware and backdoors in network protocols or to uncover rootkits hooking up API calls, the main challenge for an attacker to use HookME against you would be getting access to your network first.