There are many router models out there and the one that your ISP gives to you sometimes does not include the router IP address, they come with an auto installable kit instead.
Entering a router IP address into your web browser toolbar will take you to the router interface, this is very useful to change the router default settings and others.
A router IP address can not be changed, this is embedded into the hardware by the manufacturer, a router of the same brand and series will use the same IP, which means that it is not secret, anyone using the same router as you and in range, could connect wireless to your router interface and modify the settings, you should always change the default router password.
Step 1 to find router address:
Open Windows run and type cmd.exe OR command.com, alternatively, if you can’t find Windows run search for cmd.exe OR command.com

Step 2 to find router IP address:
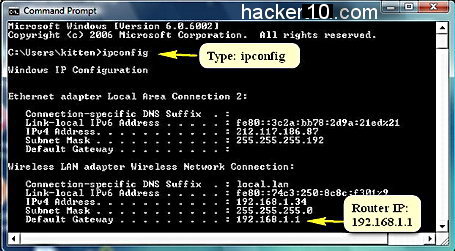
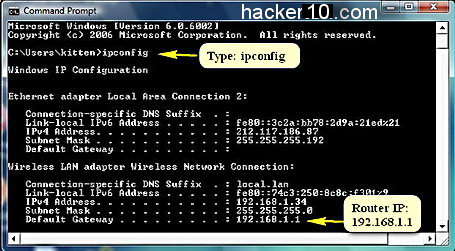
At the Windows command line prompt type ipconfig you will now see your computer Internet IP, IPv6, MAC address and router IP address.
The router IP address is the IP written right after where it says “Default Gateway” , you can notice in the picture that there are two default gateways, this is because the router is wireless and has more than one connection port, the RJ45 ports belongs to the wired ethernet connection (in this case empty) and the other port is a default router gateway belonging to the Wireless connection.