Firewalls explained
Your computer is open to attack from the moment you connect it to the Internet, even if you do not do anything with it, if the computer IP is visible on the Internet that is all that it is needed for a malicious hacker to attempt a break in.
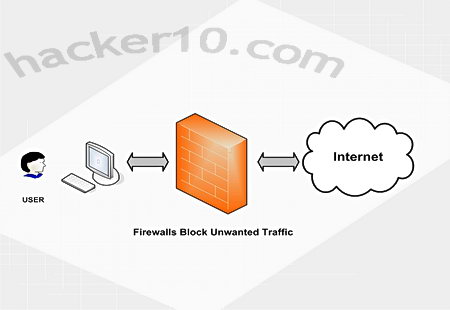
A firewall is designed to shield a single computer or private network through a set rules that permit legitimate communications to pass and stops non authorized connections, firewalls regulate traffic in and out of the network using packet filtering, a proxy service or stateful inspection. A good firewall will deny unauthorized incoming requests probing all of your computer ports trying to find one of them open to launch an attack.
Companies dealing with highly confidential data, i.e. banks, implement strict firewall rules in their network only allowing employees access to one part of the network and stopping them from accessing sensitive areas. The most advanced firewalls have the ability to ban content based on the words used to perform a search, they also make use of updated URL blacklists containing unsuitable websites, these options are meant to stop network users from coming across inappropriate content and wasting time on non productive websites.
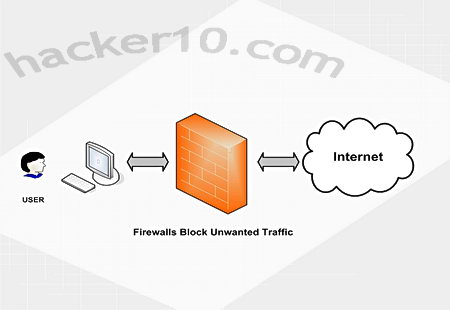
Home users tend to use software based firewalls, this is secure enough, schools and corporations with a large computer network will use a hardware based firewallnot having to install it on each one of the computers and being able to set it up inside a dedicated IT room instead of next to the computers.
How to Access Windows Firewall Settings
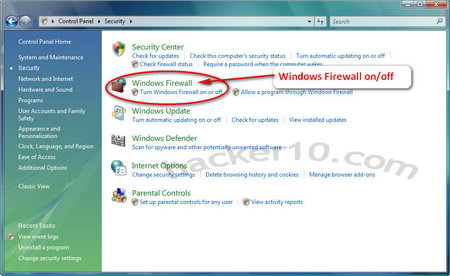
The Windows operating system included a built in firewall starting in Windows XP, to locate Windows Vista firewall go to Start(Windows logo)>Control panel>Security>Windows firewall>Change settings
Using Windows security control panel you can turn on and off your Windows firewall which is activated by default unless you change the setting during the operating system installation. The Windows built-in firewall is very basic and it lacks advanced configuration in comparison to third party software firewall packages, Windows firewall will only protect you from attacks coming from the outside, if a trojan manages to lodge in your computer and wants to send data from inside your computer to the outside world, Windows firewall will not warn you of the nasty outgoing connection.
To update Windows firewall you need to go to Start>All programs>Windows update, the Windows firewall updates itself using Windows update, it does not have any special update button.
If you install a second software firewall in your computer you should disable Windows built-in firewall, as their traffic filtering rules may conflict with each other, most software firewall will automatically disable Windows firewall during installation.
Most popular free firewalls
- Agnitum Outpost Security Suite: Free lightweight all round security suite including antivirus, antispyware and antispam features, its default settings are enough for most users needing very little tweaking, for more information read my Outpost free Security Suite review.
- Comodo firewall: Comodo firewall is available for download as a standalone program or bundled with Comodo Internet Security Suite, the later providing antivirus and anti-malware protection too. Comodo Firewall will cross-references any new software you download with a whitelist of over 15 million trusted files and applications.
- Online Armor free firewall: It prevents and removes spyware, very easy to use without too many annoying popups, Online Armor guards itself and other software from tampering by third party applications and it dettects keyloggers.
- ZoneAlarm firewall: This free firewall will resist malware attacks, its SmartDefence Advisor reduces the number of pop ups you get, comes with automatic Wi-Fi security setting activation, antiphishing protection, a toolbar, 2GB of online free storage, an antivirus and parental controls.