SandCat is a free portable penetration testing browser based on Chromium, the rendering engine behind Chrome browser, thanks to extensions support you can quickly find out what server software is being used by a website, run javascript in the loaded page, view cookies and links, use a cgi scanner, HTTP brute force a page and much more. Three tabs at the bottom of the browser allow you to easily change view from normal to source code or logs.
Coders can create their own browser extensions with HTML, CSS and Lua (a programming language), Syhunt, the browser developers, own RudaScript library allows you to execute any scripting language, like Ruby, Python, PHP, javascript, etc.
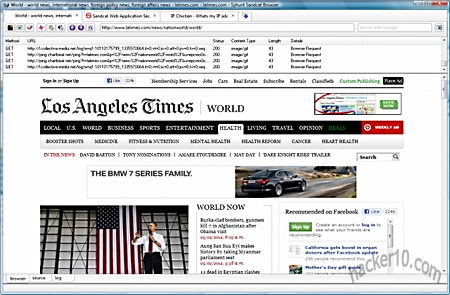
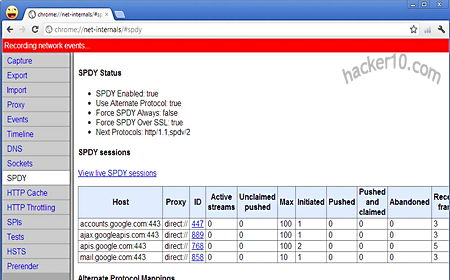
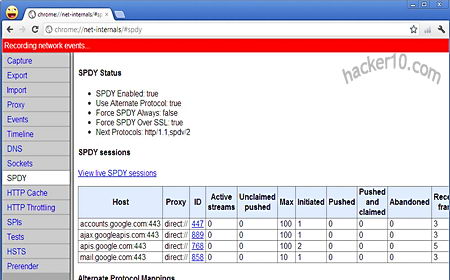
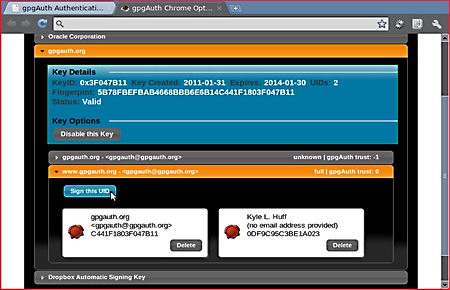
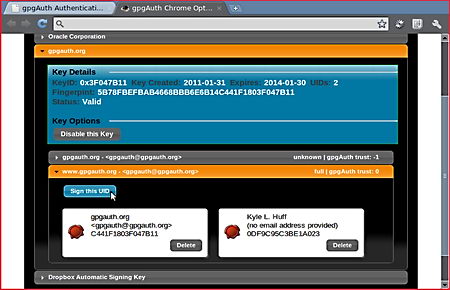
Although the browser is directed towards system administrators to test their own web server security and people scrutinizing pages that contain malware, privacy activists could use SandCat to see in real time how they are being tracked on the Internet, the browser can split its main window in half to show all HTTP live headers in real time on top of it, it can also be used to teach people how websites work, looking at the HTTP headers as you browse a website shows all of the external elements being download, packet sizes, request methods (GET/POST), pings, advertising networks, redirects… It is much more clear than seeing a website activity using a packet sniffer full of binary numbers that have to be grouped together.
The browser is too technical for the average user, unless you are a student, hardcore geek or professional PEN tester it wouldn’t make much sense for you to run SandCat.