DNSQuery Sniffer is a free Windows application that captures your computer DNS queries, the program is useful to troubleshoot name resolution complications and check if a domain name is being blacklisted by your ISP DNS. There is no need to install the program, you can run it in portable mode and carry it with you on a USB thumbdrive.
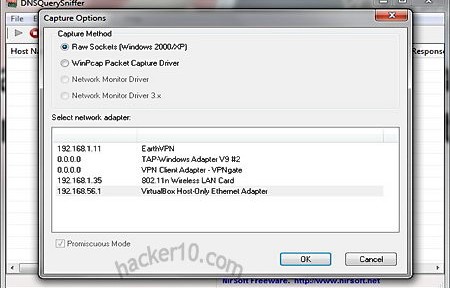
When you run DNSQuery Sniffer for the first time you will shown the available network adapters in your computer, including virtual host components presented as a separate network cards. Your initial choice of capture options will be set as default, to change them later on you will have to access Options>Capture Options or click F9, there are shortcuts to access many of the functions.
I recorded my DNS queries while on a VPN and it worked perfectly well. A VPN encrypts data in transit over the Internet but recording takes place before DNS queries leave the router. Another use for this program could be for a system administrator to spy on network users, if you are using a portable VPN on an Internet Cafe, DNSQuery Sniffer is one of the many tools a computer admin can deploy to monitor in real time at what sites you are visiting.
Some of the details recorded include Host name and port (for example: pagead2.googlesyndication.com:54630), DNS query time stamp, request time and response time, reverse DNS lookup, IPv6 server address, destination IP address and many others. I noticed that most of the requests only show hostname and port, itemised displayed details will depend on what server you visit.
While I was recording outbound queries on my computer I was able to see Google Adsense and Facebook queries created by the plugins embedded in the website I just visited. Logs can become huge within a couple of recording hours, they can be exported as CSV/XML or HTML file and import them into a spreadsheet for processing.
This tool will be useful for system administrators. Home users without logging needs might prefer to troubleshoot DNS problems with another freeware called DNS Benchmark.