New top secret documents leaked by Snowden (link below) reveal that GCHQ, Britain’s spy agency, has a team to reverse engineering popular encryption software and they routinely collaborate with British police when they come across encrypted data during the course of an investigation. Since it is not needed to explain in court how law enforcement has managed to access the encrypted data, it can remain secret when GCHQ finds a vulnerability in an specific program.
In one particular case, GCHQ assisted the National Technical Assistance Centre, a domestic law enforcement agency, to decrypt child pornography stored inside a virtual encrypted container created with Crypticdisk and in another case, GCHQ cracked Acer eDataSecurity Personal Secure Disk for an undetermined “high profile police case“.
Acer eDataSecurity is a free file encryption utility that comes with Acer laptops. I was not able to find out what algorithm Acer is using for encryption but I learned reading the laptop manual that the user can choose a bit strength of in between 128bit and 256bit, the manual textually says that “If you lose your password, there will be no way to decrypt your encrypted file!“, it has not been designed with a backdoor, deducing that GCHQ cracked it on its own without assistance from Acer.

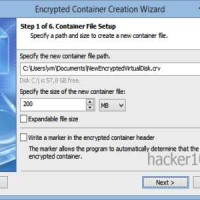
The other cracked software, CrypticDisk, from Canadian company Exlade, has thousands of companies and government agencies as customers. CrypticDisk can create a virtual encrypted disk or encrypt and external device, like a USB memory stick, where you can store data or programs, once the container has been closed, it is meant to be inaccessible, it works like Truecrypt and the company page mentions that CrypticDisk encryption keys can be made of up to 2944-bits in strength, with built-in support to open Truecrypt containers.
CrypticDisk containers can use multiple encryption algorithms in cascade, there is a selection of AES, Twofish, Serpent, Blowfish and CAST6. The encryption wizard advises that the more algorithms you choose in cascade, the higher the cryptographic strength.
There isn’t any clue in the leaked papers about how GCHQ cracked this software, I will make a guess of a bad implementation because the encryption algorithms are all open and AES has been widely reviewed by expert cryptographers. I am discounting the possibility of a user mistake choosing a weak password because British police is known to have a computer cluster where they can try thousands of dictionary words per minute, theoretically there should be no need for the UK secret services to help out law enforcement brute forcing a passphrase.
The same secret documents reveal that GCHQ has obtained a warrant from the Foreign Secretary so that they can not be prosecuted for breaching copyright law from proprietary software companies. The agency is also targeting antivirus companies to be able to send trojan horses to targets without being detected. KasperSky, a Russian antivirus company, is named in the documents as being a challenge to them.
Snowden documents: https://firstlook.org/theintercept/2015/06/22/gchq-reverse-engineering-warrants/
Leave a Reply