VoIP calls are transmitted over the Internet unencrypted, the data packets can easily be intercepted by a malicious hacker to record the calls and listening in, a simple packet sniffer like WireShark is all that it is needed to eavesdrop on a VoIP call, no high skills are involved.
How to encrypt VoIP calls
- Use Zfone to add encryption to your VoIP client: Zfone works on top of your unencrypted VoiP software watching for VoiP data packets going in and out of your computer, when it finds them it ciphers the packets encrypting the VoIP call, there is also a man-in-the-middle (MiTM) attack countermeasure by displaying a short authentication string for the user to verbally compare over the phone witht the other end, Zfone is open source software using the ZRTP protocol, there are no backdoors of any kind included.Before considering Zfone to secure your VoIP calls have into account that the software must be installed by both callers and Zfone does not work with Skype because Skype uses a closed source protocol not compliant with the standard VoIP protocol.
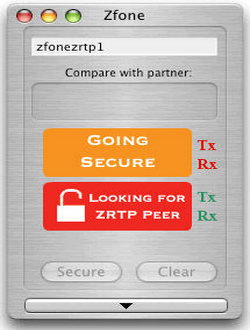
Zfone VoIP encryption software - Use a Virtual Private Network (VPN): A VPN like HMA can encrypt all of your internet traffic routing it through their encrypted OpeVPN tunnel, this will include all of your VoIP calls. Routing your VoIP calls through a VPN will slightly increase the bandwidth requirement and produce some CPU overhead.One benefit of using a VPN is that if your ISP or a corporate firewall is blocking VoIP calls using a VPN for VoIP will get around Internet filters, they won’t even know you are making a call, it will also get around state sponsored surveillance which is normally carried out at ISP level.

Wiretapping VoIP password - Use VoiP software with built in encryption: Some VoIP clients like Skype have built-in encryption used to cipher VoIP data packets, if you adopt this solution to secure your phone calls, try to choose voice over IP software compatible with as many other VoIP clients as possible using open source encryption (not Skype) this will make it much harder to introduce a backdoor and it might not require the other end to have the same VoIP client installed for encryption to work.VoIP software using encryption: PhonerLite ; TiviPhone