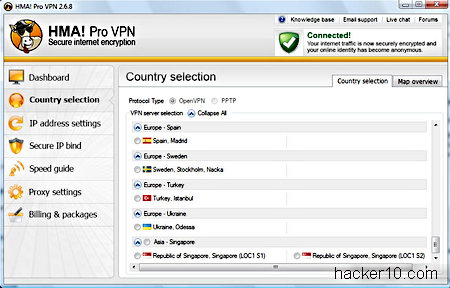
I have been using Hide My Ass VPN service for a year now, during all this time I have seen some servers come and go, mostly come, there has been a considerable increase on server locations. One thing that makes HMA premium VPN service stand out from the crowd it is their vast number of servers and IPs available.
I am based in Europe using a 10MB ADSL pipe and most of HMA VPN European, USA and Canadian servers almost match my original ISP speed, only the Singapore servers seem to be considerably slower all the time as well as having a huge ping rate (ie. lag). But your results will likely be different depending on where you live, choosing the location of your VPN as close as possible to your home considerably improves VPN speed and ping rate, if you are in Western Europe for example, and want to use a USA VPN, choosing a server on the East Coast of the US should improve performance a great deal.
The only place where I have found some of Hide My Ass USA VPNs blocked is while watching Hulu, you can easily get around this block by choosing a different US server of the many others available.
Hide My Ass company headquarters
My biggest grudge against HMA VPN it is the way they hide where their headquarters are, they don’t seem willing to reveal in what country they are based and this is pretty important because when you use a VPN three country laws must be abide for, the laws of the country where the VPN server physically is, the laws of the country where the VPN company headquarters are and your own (user) local laws.
The user local laws don’t really matter much because nobody knows where you are unless the VPN company reveals it, but the first two matter much more because it is trivial for a law enforcement agency or RIAA outlet to find that out and if HMA headquarters are located in, for example, China, then they must abide by Chinese law, it is not good enough to keep this secret. Users should be informed of where the VPN company headquarters are located.
For all that is worth, I would place my bets that Hide My Ass company headquarters are in the United Kingdom because HMA website DNS servers are using ns1.zymic.com Zymic being a hosting company that uses the tagline UK/US on its Twitter account and contains a link to HMA VPN service on its homepage footer. The Zymic domain is also registered in the UK by Netco Solutions but it appears to be a privacy registration.
The biggest give away is that HMA VPN affiliate program pays out using a British bank account, draw your own conclusions from that. I guess they must be paying their taxes somewhere.

Hide My Ass VPN receives DMCA complaint
Various people at HMA forums have posted that Hide My Ass sends out warnings when a complaint is filled due to illegal filesharing activities, HMA as it is their legal duty, complies with the law and hands out a notice so that the copyright infringing torrent is removed. This is a good example that if necessary Hide My Ass will track you down, like any other VPN service will, at least HMA will give you a chance to remove the offending file and not terminate your account straight away.
You can still use HMA for filesharing as it is not against their terms and conditions but using a USA server for doing that is not too clever, specially since HMA has a server in Russia where filesharing of copyrighted movies does not break any local law, to be safe, make sure that whatever activity you do is legal in the server you are using so that no complaint can be filled.
If you think that you can carry out illegal activities and get away with it because you are using Hide My Ass VPN, think again, according to their privacy policy, HMA keeps connection logs for up to two years, ,more than enough time to track you down.
Many VPN services claim to not store any logs, but they will actually produce them when pressured by the authorities because all of the VPN activities get traced back to them. Using a VPN makes the job of tracking you down harder but not impossible, to make it impossible use a tor proxy.
Hide My Ass VPN service advantages
Hide My Ass has dozens of VPN servers and thousands of IP available all over the world, there is no bandwidth limit you can download as much as you like, torrents are allowed, their VPN speed is more than reasonable for the average user and it gets through geolocation based online TV blocks.
Their email support has normally replied to all my queries in around 24 hours, normally concerning servers that have stopped working, they eventually get fixed, not a big deal.
Forget about the forums for support, you will not get real tech support there, in case of problems use Hide My Ass VPN export the logs and send them via email to HMA support.
Hide My Ass VPN service disadvantages
Your IP can be exposed if your VPN connection drops and you get no clear warning whatsoever, you can be surfing the Internet with your real IP after a VPN disconnection and you will not be aware of this. There is a secure IP binding feature in HMA VPN client but it did not work for me and even if it worked that feature does not support all Internet applications.
Paying HMA VPN monthly is on the high side of prices and Hide My Ass homepage advert of a 60% discount saying “offer expires soon” is a total lie, that offer was there one year ago when I signed up for it and it is still there now, it has never gone offline at any moment, this does not say too much about HMA honesty.
I am not a big fan of Hide My Ass VPN management software either, it seems clunky to me, but you can put that down to personal taste if you like, I am not into fancy graphics, I rather have simplicity.
Conclusion Hide My Ass VPN review
Assuming you pay yearly their VPN service is great value for money, you have numerous server locations to choose from, coverage is a little scarce for Asia but that is the norm at most VPN providers, something to do with bandwidth availability and expensive server prices in that part of the planet.
HMA VPN support is fine and server reliability pretty good, with so many servers if one does not work just choose a different one, I am just not too happy the way they seem to hide where their headquarters are, I like to know where my VPN provider company is and if possible who is behind it, and I am not too enthusiastic about a yearly commitment either, which is when HMA VPN prices become affordable, that is why I am not going to renew my yearly subscription when is up, I would like to try something else and see how it goes, I am always on time to go back to HMA, it hasn’t been a bad experience, they just have a little room for improvement.