YaCy is an open source community based search engine written in Java with no central server indexing the results, search queries are produced using a worldwide peer to peer computer network, in the same way that torrent downloads work, the quantity and quality of the results will depend on the number of peers connected at the time, on top of the search results YaCy lets you know how many peers are providing them, it can be used to search text or images. Unlike Google or Bing, where the company managing the search results is open to subpoenas and censoring links (e.g. DMCA complaint, offensive images, etc), YaCy results can not be censoredas no single central authority is responsible for them and there are thousands of servers (personal computers) in multiple countries providing results, with some seed list servers including accurate p2p node information to be found in the source code.
You will need to download YaCy software to your computer to use it, during installation Windows default firewall will be configured to allow YaCy queries pass through, if you are using a different firewall you will have to set it up manually to allow YaCy to connect to the Internet. The search engine will be accessed in your browser clicking on YaCy’s logo or visiting http://localhost:8090 (default port can be changed), YaCy can be set up to crawl an specific website or FTP server creating your own search index, the crawling can be scheduled to as often as you like or limited to a single time to save computer resources.
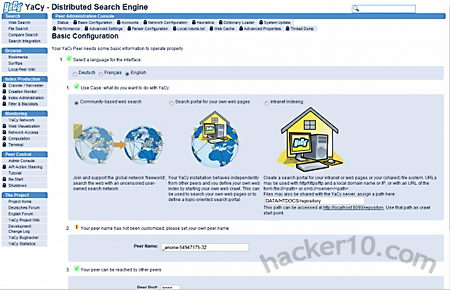
To protect your privacy after performing a search the words used are sent to a peer in the form of distributed hash tables, peers store crawled search results as cryptographic hashes and these are all mixed in between peers, making it impossible to pinpoint search queries to a certain host. Search is not limited to the public Internet, YaCy can be used in Intranets, the configuration settings had so many options that it can take a long time to understand what everything is for, the best is to leave the defaults.
In my experience YaCy Internet results were not very good, with a tendency to link to deep pages instead of the main portal, my main predicament is that it did not have too many pages indexed and it took a couple of seconds to finish each search query, this can be improved once YaCy manages to reach a sizable number of users/peers. Until then, this search engine will be better suited for Intranets or custom crawling of forums and wikis, admittedly, their plan is not to beat Google results, but to provide a truly private search engine experience. There is no need to erase logs, because there are no logs and companies do not have to rely on a third party server to run their private search queries. In the future the developers plan on indexing tor node pages and Freenet sites.