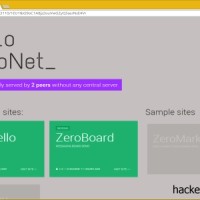
Zeronet is an open source decentralized peer to peer webhosting platform using cryptographic hashes and torrents to distribute websites and files. Any computer with an Internet browser and the software installed can access websites hosted in Zeronet. When you first launch your browser you will not see any IP in the toolbar, a Zeronet website is served from your own computer after downloading the files, your browser toolbar will show localhost:43110 and a cryptic address, supporting .bit domains, a peer to peer top level domain name managed by a decentralized registrar called Namecoin.
To make a website available in Zeronet you only have to host it in a single machine, visitors to the site will help distribute the content from their own computers when they view the pages, the more nodes/visitors a website has, the quicker it will be for others to download it, scalability is easy, when a site becomes very popular files are available from multiple sources.
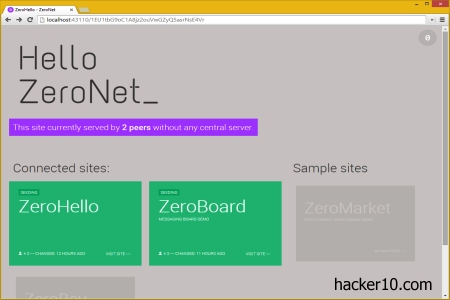
Zeronet users can see in the interface what websites they are seeding, how many peers it has and right click on one of the sites to update, pause or delete it from their system. Cryptographic hashes verify the integrity of the files in the website, it tells Zeronet what to download and protects from man in the middle attacks. When you upload a website to the network you will be handed over a private encryption key for when you wish to modify and update the content, visitors automatically use the public encryption key to verify that the files have been changed by the rightful owner.
The network is not truly anonymous, but their websites are quicker to download than hidden Tor sites, optionally you can run Zeronet over Tor to hide your computer IP from anybody tracking file downloads although this will slow it down. Zeronet also comes with a guestbook and forum where to debate and post links to internal websites that are not accessible using the regular Internet, only people with the software installed can access websites.
Zeronet should work very well for Chinese surfers craving for information about the national liberation struggle in Tibet, but if the content is banned worldwide, this network isn’t going to cut it. Since it is possible to find out what computers are hosting the content, authorities can knock on the door of people distributing those files until not a single one of them is left.
Personally, I don’t believe in censorship resistant networks that don’t provide anonymity by default and I am skeptical of the need for this project when Iranian or Chinese users can download a VPN proxy to access banned information instead of using Zeronet with access to a limited range of websites.