Every time you enter a URL in your computer browser a DNS query takes places and asks your Internet Service Provider to translate the typed in letters into an IP address so that you can visit the website, this is what is called a DNS query and if you happen to be in a country that censors the Internet or practises mass surveillance the sites you visit can be watched in real time. It is also possible for a spy agency or malicious hacker to sit in the middle of DNS queries and show you a fake website when you try to visit certain URL, then proceed to capture your login and password or serve malware to your computer.
The most common use for DNS monitoring it is Internet filtering, schools and companies do this to fend off adult material and the Chinese Great Firewall does this to block news websites about the Tibet.
The programs below come preconfigured with dozens of free DNS servers, a few of them have built-in parental controls to protect your kids, others offer censorship free DNS queries and do not log any activity, with the most security conscious offering encrypted DNS queries. The advantage of using one of these programs to change your ISP DNS servers, over doing it manually, is that it only takes one click and you don’t have to search DuckDuckGo for free public DNS providers.
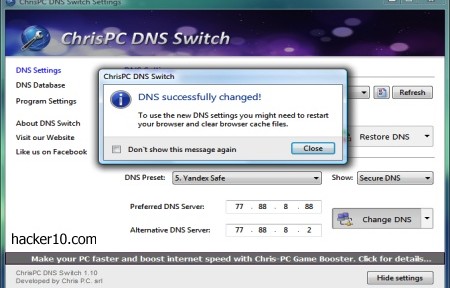
ChrisPC DNS Switch: It comes with more than two dozen free DNS providers, one drop down menu allows you to select the network adaptor and another drop down menu classifies the DNS providers into “Anonymous” (no logs), “Family Safe DNS” (URL filtering), “Secure DNS” (malware filtering), “Regular DNS” and “Custom DNS” where you can manually enter the name server you would like to use.

DNSCrypt Windows Service Manager: A DNS encryption only DNS changer, it helps you configure your network adaptor with one of their supported DNS encryption providers. At the moment consisting of DNSCrypt.eu in Europe and claiming to keep no logs, OpenDNS in the USA, CloudNS in Australia and OpenNIC in Japan. You are also given the option to choose UDP/TCP and IPv4 or IPv6.

QuickSet DNS: A minimalist Windows utility to change the DNS settings of your computer or router. This is one of the few DNS changing utilities that allows you to change your router DNS using a graphical interface. Optionally you can also use QuickDNS from the command line.

DNSJumper: Windows DNS graphical interface where you can select the DNS of your choice out of a long list of public DNS servers (Comodo DNS, Norton DNS, Google DNS, etc). To change DNS settings often the program lets you flush the previously applied name servers with the click of a button.Clicking on the “Fastest DNS” button will automatically find the most expeditious name servers for you.

If you are using a VPN to encrypt your connection your ISP could still be able to see what sites you visit monitoring the DNS servers, this is know as DNS leak. To avoid this risk you should change the default DNS servers in your router or computer. For extra security you should select a DNS provider that encrypts queries, it is the equivalent of HTTPS for DNS.
Note: If the DNS program does not have a DNS flushing button you can flush your DNS cache manually in Windows with: ipconfig /flushdns