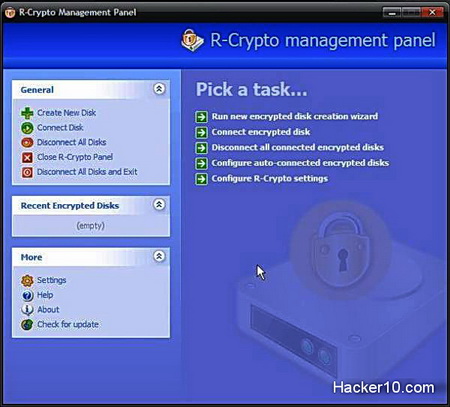
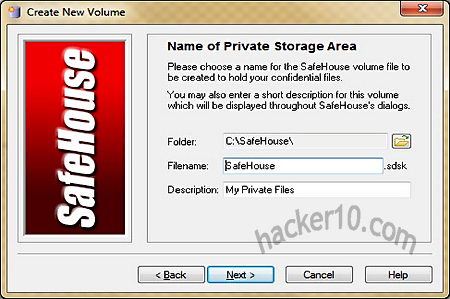
Not the most original of the names, File Encryption is an open source …
There are zero AI articles in this blog. I write about privacy and security online, I don´t earn a living with this blog so I write what I want, there is no leverage on me.