Recently released Snowden’s NSA documents published by the German magazine Spiegel reveal the NSA has a dedicated team to crack VPN traffic and feed it to their data mining software. The documents list over 200 commercial VPN providers, like Astrill, CyberGhostVPN, iPredator and PrivateInternetAccess (PIA), they include companies that no longer exist like Xerobank and also name small VPN providers.
One of the leaked NSA slides says that copyright violators, pedophiles and Internet scam artists all use Internet anonymity, highlighting that terrorists using anonymity are the NSA main concern, however, this is a three year old document and contemporary news indicate that the NSA and GCHQ now also have orders of using their skills to hunt down pedophiles on the Internet.
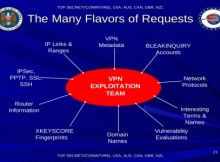
The 51 pages long slide titled “Internet Anonymity 2011” starts explaining the differences in between encryption and Internet anonymity, contrasting how encryption hides content and VPNs hide metadata, which is important for the NSA. There are commentaries in favour and against Internet anonymity and it briefly introduces the different proxies and VPN protocols available (PPTP; SSH; OpenVPN; L2TP; SSTP).
A short analysis spells out how commercial VPN providers work and exposes that the NSA is listing all servers VPN providers have, with a noted complaint about a free VPN provider called HotSpotShield because their list of servers is not readily available for the NSA and the staff has to reverse engineer them.
After VPN traffic has been decrypted, everything is stored in XKEYSCORE, a Google like supercomputer used by the NSA to quickly search for specific words or computer IPs.

To crack OpenVPN the NSA advises to use XKEYSCORE with X.509 digital certificates, it then shows some real examples of how they fingerprint HostSpotShield, Easy hide IP, Comodo VPN Trust Connect and SecurityKiss, enumerating the ports each service is using with references to their RSA key. Other documents mention that the NSA is aiming at processing 100,000 requests per hour by 2011, this means that they should be able to decrypt and reinject data of 100,000 VPN users, a capability that I am guessing will have considerably increased since then.
There are comparisons in between single hop proxies, picking as example Psiphon, multihop proxies that pick JonDo as example and Tor, the comparison lists the advantages and disadvantages of each one of the methods and ends with the conclusion that Tor remains the safest anonymous proxy available.
According to the NSA, “sophisticated targets” use Tor to access terrorist forums, it specifically names the terrorist forums al-Faloja, CEMF, al-Hisbah, shumukh, using this as the main reason why the NSA needs to identify Tor traffic, which apparently is hard to do. The only breakthrough the NSA mentions is the capability they have of identifying a few Tor servers, due to their unique characteristics of random digital certificate issuers and the certificates being always only valid for 2 hours.

The secret documents call the Torbutton a “thorn in the side of SIGINT” (intelligence gathering) because it disables all active content and they have no work around. To crack Tor the presentation recommends “implanting a web server with poisoned content intended for target“, which in plain language means getting the target to download a file infected with a trojan horse.
A different 43 pages long NSA presentation gives more technical details about VPN traffic cracking and they mention that all branches have a specialist VPN representative to spy on a target. The same presentation says that the VPN team provides vulnerability analysis and suggests alternative approaches if exploitation is unrealistic. In one particular slide, the NSA stresses in capital letters that VPN exploits are POTENTIAL, depending on many different factors.
The second presentation illustrates the NSA success cracking PPTP traffic and goes onto name Iran Air, the Afghan government, Turkish diplomats and Kabul bank as some of those using PPTP to secure their communications. The NSA justification for spying on bank communications is that by following the money they find who is at the other end. And one very important reminder adds on the last page that “If it’s not exploitable now, that doesn’t mean it won’t be later“.

PPTP has been considered insecure for a long time, these documents not only confirm it, they also illustrate that it is being exploited on a daily basis. If you use a VPN make sure to only connect with the most secure protocol, OpenVPN. A second security measure should be to only sign up with a VPN company that has competent security staff, the NSA VPN exploitation for OpenVPN appears to rely on finding the pre-shared key.
Other jewels found on the leaked documents are that the NSA admits to not being able to crack PGP encryption and OTR (Off-the-Record Messaging), two of the documents show metadata without any transcription for the conversation, marked by NSA staff with the sentence “no decrypt available for PGP encrypted message“.
As for remailers, the “Internet Anonymity” NSA slides disclose that the agency considers Mixmaster and Mixminion the most secure remailers due to their high latency, adding that they are hardly used by anybody.
Without a doubt, the leaks show that the NSA has lots of interests in wiretapping VPN traffic. People worried about illegal spying could stick to Tor since the NSA admits that they can’t crack it, but a different GCHQ (UK secret service) presentation leaked in the same article and titled “potential technique to deanonymise Tor users“, mentions that the UK secret services is considering using Tor exit nodes they own to help them deanonymise Tor users, the presentation is highly technical and appears to be a future project, that, if it has been implemented, means that the GCHQ has deployed their own honeypot Tor exit nodes to log all traffic and with it any passwords you enter.
I can only see two solutions for the paranoid, one of them, is using double authentication to login to the VPN, you could use a key based SSH login with PuTTY, this places the encryption keys in your power and not in the server, this way only a trojan horse could steal your keys. The second solution, is to combine a VPN with Tor, which will slow down your Internet browsing.
More information: http://www.spiegel.de/international/germany/inside-the-nsa-s-war-on-internet-security-a-1010361.html