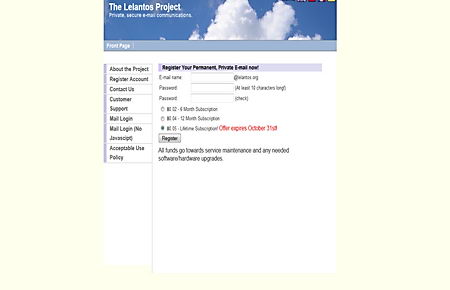
Lelantos is a privacy email provider only accessible through Tor but able to communicate and receive messages from any Internet wide email services like Gmail or Yahoo. The owners, a small unidentied group of people, claim that all data in the server is encrypted, with data back ups located in different countries.
When you open a Lelantos email account you will initially get a @lelantos.org address, currently that domain name is registered to someone called Ryan Harris living in Canada and the DNS servers are set to Domains4Bitcoins, the little information one can gather from that is that Lelantos is paying the domain registration with Bitcoins, registration details in Canada might be fake or might not.
To stop other people from knowing that you are using a Tor email service Lelantos gives you a choice of multiple private clean domain names that are not listed anywhere and not linked to the Tor network. Lelantos obviously doesn’t have access to your computer IP since the only way for you to read and send messages is using Tor.
Lelantos webmail has two interfaces, a SquirrelMail layout that does not need Javascript enabled to login and a RoundCube interface that needs Javascript. I have used both interfaces and there isn’t too much difference in between them, RoundCube, looks more modern and has drag and drop but the main functions work the same. If you are serious about privacy go for the SquirrelMail interface with no Javascript.
Another way to protect yourself against browser exploits is by using Lelando’s IMAP and SMTP .onion servers with TLS, for this you have to set up your email program with a socks proxy and run Tor in your computer. Unfortunately few email programs support socks proxies, I suggest the free open source Thunderbird email client from the Mozilla Foundation.
Lelando’s terms and conditions forbid using their email service to transmit child pornography, spam or sending violent threats, if you breach their Acceptable Use Policy your account could be terminated.
This is not a free email provider, you have to pay some Bitcoins to fund service maintenance, I think that it is not unreasonable since they also provide support, with a public PGP encryption key available to communicate with Lelantos staff. For extra security is best to anonymize your bitcoins with a laundering service like Bitlaundry, but, as long as bitcoin payments can not be linked to an specific email account it should be fine.
Lelantos Tor address: http://lelantoss7bcnwbv.onion