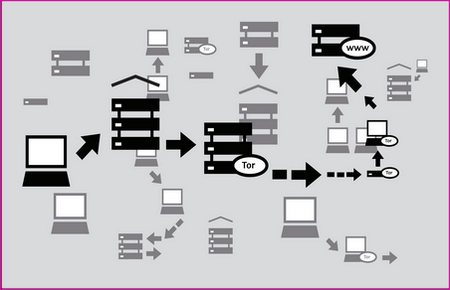
Whonix is an anonymous operating system based on Virtual Box, Debian Linux and tor proxy, Whonix consists of two virtual machines, one dedicated to run a tor proxy acting as a gateway and the second one called Whonix-Workstation located in a completely isolated network.
The system has been designed to make IP and DNS leaks impossible, not even malware with root access will be able to find out your computer IP, all Internet connections are forced through tor, including applications that do not support proxy settings, this is done using the firewall settings. It is possible to use Whonix with a VPN or SSH tunnel if needed, hardware serial numbers are also hidden. Any operating system able to run VirtualBox can run Whonix, this includes Windows, Mac, Linux, BSD and Solaris.
Disadvantages of running Whonix are that it will be very slow to update your operating system though tor, it is more difficult to set up than the tor browser bundle and your computer should have a good amount of RAM and modern CPU to run VirtualBox. Whonix advantages are that unlike an anonymous live CD like Tails or Liberté Linux data will be available after reboot due to persistent storage, you can install your favourite software packages using Debian’s packaging tool apt-get, the applications will be torified straight away, you can also save virtual machine snapshots saving a clean one for data recovery if needed.

Many Whonix default applications come configured to avoid fingerprinting, GPG software for example will not reveal your operating system version and XChat comes with the default torified set up as described in the tor project Wiki.
In countries where you can be forced to disclosure your full encryption password Whonix can help with plausible deniability if you hide the .ova virtual machine file inside a hidden encrypted container with Truecrypt or store the virtual machine inside a fully encrypted USB thumbdrive that will look like random data to forensics software.