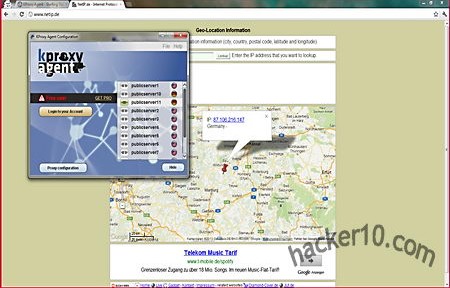
KProxy Agent is a Chrome based portable browser that comes preconfigured to handle HTTP requests through one of the free KProxy network of IPs to bypass Internet filtering. People using public computers at work and college will find it useful to access Facebook, YouTube and other typically blocked entertainment sites. The browser runs in Incognito mode by default (known as Private Browsing in Firefox). Chrome Incognito mode executes in RAM memory and does not store browsing history, cookies or cache in the hard drive, browsing traces will be gone and non recoverable after you close KProxy Agent, the developers claim that proxies encrypt data in between the browser and the sites you visit, any passwords or email you send can not be intercepted by anyone listening in, which makes this tool suitable for security in public Wi-fi access points.
The speed tests I carried out on the free proxies gave me around 2MB-4MB, this is enough to watch online TV, taking advantage of this I managed to bypass geoblocking filtering and I was able to watch Hulu from outside the US without problems, unfortunately the ping rate wasn’t so impressive and browsing Internet sites at times it felt slow, I solved it by choosing a different proxy server closer to home.
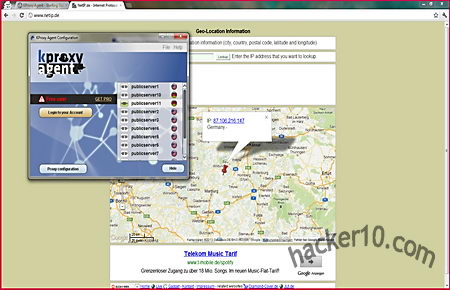
KProxy Agent has been developed in Java, it will not work if this is not installed. Java has had numerous security problems in the past but it benefits from being multi platform, this portable browser will run in Windows, Mac and Linux or any other OS that has Java installed. Switching in between proxies can be done in a matter of seconds within a couple of mouse clicks but only US and German proxies could be found in the proxy list. KProxy Agent could benefit of a more detailed proxy information, instead of having ten different public proxies with the American flag next to them they could point out where exactly in the US each proxy is located, East or West coast and enumerate server load for each one of the proxies so that the user can choose the best one.
It seems that KProxy Agent developers intend to make money with this program by getting people to upgrade to their faster premium proxy service, you will find KProxy Pro mentioned around but in a non obstructive way, if you only use an Internet censorship bypass tool occasionally the free version is just fine, you only need to trust KProxy owners with your data just as it happens with all other proxy or VPN services.