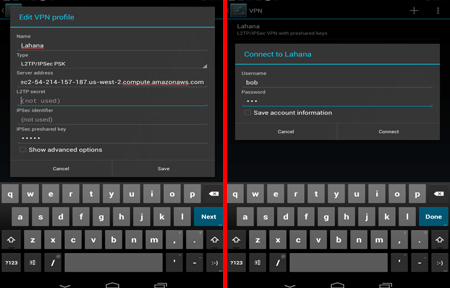
Lahana is a set of scripts that can quickly create a VPN on Amazon EC2 cloud servers using Linux instances and tunnel everything through the Tor proxy network. It defeats state level Internet censorship, thwarting DNS poisoning used in the Great Firewall of China and blocking of websites by ISPs blacklisting URLs. The only way to stop Lahana is by barring access to all of Amazon EC2 servers which would leave the whole country without a cloud platform used by many companies providing different services or censors could block a single node and play a whack-a-mole game where the user gets access to a new Lahana proxy node from someone else everytime one of them is blocked.
There is no need to install any software for the user, Lahana can be used in Mac OS X, Windows, iPhone and Android, it should work on any device with a built in IPSEC client able to set up an L2TP VPN tunnel,. VPN node credentials can be publicly shared or only given to trusted individuals. The developer’s explanation to use Tor as exit node instead of Amazon servers IP is to protect the operator running a VPN on Amazon EC2 from abuse, if anyone commits a crime with the a Lahana VPN it would lead back to a Tor IP address and not the VPN operator. Lahana VPN sits in the middle in between the user and Tor in the form of User>>Lahana VPN>>Tor>>Website.

Lahana nodes also serve as bridges and can be used to access hidden Tor websites, the more Lahana VPN nodes there are up, the faster the Tor network gets. This tool solves the Internet censorship problem but not privacy or anonymity, it would very easy for a Lahana VPN operator to log your computer IP and see what sites you visit and capture usernames and passwords, for high Internet anonymity you should only use Tor.