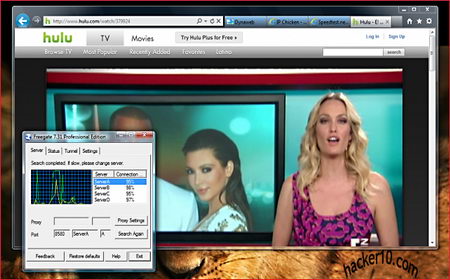
Freegate is a proxy software to enable people living in a country that censors the Internet to circumvent ISP filtering, it is one of the most used proxies in China and it is hosted in hundreds of dynamic mirrors to outsmart the Chinese authorities, you can also request a download link emailed to you as FreeGate website is obviously blocked in China. The proxy was initially created by Falung Gong followers (a spiritual discipline banned in China), developed and maintained by Dynamic Internet Technology Inc. and it receives funding from non-profit American organizations, including the US Government.
The project uses Hurricane Electric servers in California, you will get an US IP in that state when you use it, I had no problems watching Hulu (restricted to US residents) and listening to Pandora radio with FreeGate, at the time of my testing I was getting 1.5Mbp/s download speed, enough for video streaming, there are various servers available, all of them in the US, it is easy to switch in between them. The software interface looks outdated but is easy to manage, it contains a few extra options like erasing Internet Explorer history when the program exits and setting up a list of websites to connect directly without using FreeGate, it comes preconfigured to connect to some of the most popular Chinese websites like Baidu, Taobao and any .cn site without a proxy, a hotkey can be set up to hide/show FreeGate.

The program automatically opens up Internet Explorer after executing it, it is possible to configure it with other browsers but it requires some manual tweaking changing the browser network settings, or you could download Gproxy Firefox addon to help you manage and switch proxy settings. There is no need to install FreeGate in your computer, the software will run from inside a thumbdrive with a double click but I was asked for administrator rights to allow FreeGate to pass through the Windows firewall and execute Java.
Using FreeGate will not offer you the same degree of anonymity that the tor proxy does but it is considerably faster, if all you care about is bypassing an Internet filter FreeGate works very well, just remember that it has been designed for users in China, while it works elsewhere the developers are developing this proxy as a China centred circumvention tool and I doubt they will attend feedback from someone in Europe complaining that the can’t watch a US only TV film, this is also not a VPN, the only connection that will go through the proxy is the Internet browsing, all other applications (IM, torrents,SMTP) will be using your home computer IP.
Some people report that the software is flagged by their antivirus, I use AVG antivirus and I did not get any malware warning, the software does not contain any trojan but it works similarly like trojan horses do penetrating firewalls, just make sure you download it from an official link. FreeGate is a good tool to have if you are going to travel to China or any other country with Internet censorship, like Iran and Vietnam.