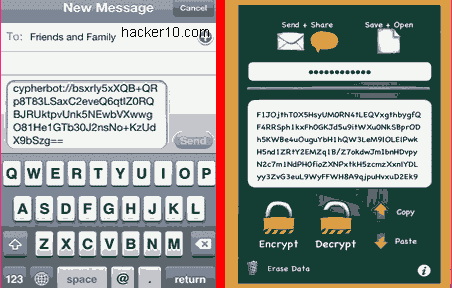
Tinfoil-SMS is a free open source Android app to exchange encrypted SMS messages with other Tinfoil-SMS users. After installation you can import contacts from your phone and all future conversations will be handled by Tinfoil-SMS but communications with contacts will not be secure until a successful key exchange has been executed.
To stop man in the middle attacks, where encryption keys are replaced by an attacker and messages forwarded after logging them, a signed encryption keys exchange must take place first. In the app menu you will see two fields labelled Shared Secrets, there you need to input two secret passphrases and save them, Tinfoil-SMS advises a minimum of 8 characters for each shared secret, you have to transmit the secret to your contact by secure means (not your phone).
The receiver will get a notification showing your phone number next to “Pending key exchanges“, he will have to enter the passphrase you have given him and from then on any future message exchange will be encrypted.
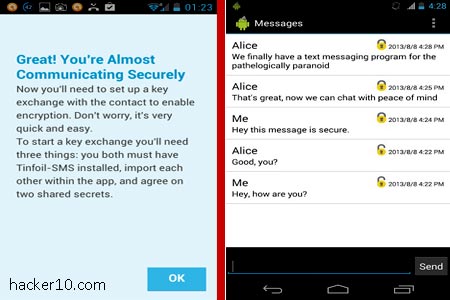
Messages are secured using AES256-bit in CTR mode, in the SMS thread you will see a padlock attesting that encryption is on. Tinfoil-SMS settings allow you disable and enable SMS encryption, manage encryption keys and delete/adding contacts. It is similar to TextSecure, another encryption SMS app, the main differences in between both are that Tinfoil-SMS signs key exchange with the shared secret, encryption algorithms are slightly different, Tinfoil-SMS cipher is AES256bit and TextSecure AES128bit and Tinfoil-SMS will not encrypt messages locally in your phone whereas TextSecure does.
The reason Tinfoil-SMS developers give to support SMS instead of real time chat encryption is that many oppressive regimes are in third world countries where people does not have data plans and use SMS messages to communicate, this has the added benefit that the app would still work if the government shuts down Internet access.
Tinfoil-SMS future plans include incorporating steganography to hide that you are using encryption. There is also planned a detailed cryptanalysis of the application which will always be free and open source.
This is an app I would trust due to its open source nature and what it looks like a good security model, with the only inconvenience of having to exchange the shared secrets by secure means before encrypted communication can be established, which can be problematic and it is likely to force some people to transmit the secrets insecurely.
You can download Tinfoil-SMS from Google Play or F-Droid, an alternative Android marketplace made up entirely of free open source software and not controlled by Google.